
Zero-Day Research: CVE-2022-41220 md2roff Version 1.9 Buffer Overflow
After multiple rounds of fuzz testing, I discovered that md2roff version 1.9 suffered from a stack buffer[…]

Zero-Day Research: PicoC Version 3.2.2 Null Pointer Dereference (CVE-2022-34556) Speedrun
PicoC is a miniature code interpreter developed for C scripting. According to their documentation, PicoC was first[…]

Zero-Day Research: md2roff Version 1.7 Buffer Overflow (CVE-2022-34913)
The best part about security research is the myriad of ways you can find bugs. Sometimes bugs[…]
HackTheBox: Baby Todo or Not Todo Challenge
Practice can be quite a double-edged sword. Most of us know that creating long-term behaviors and skills[…]
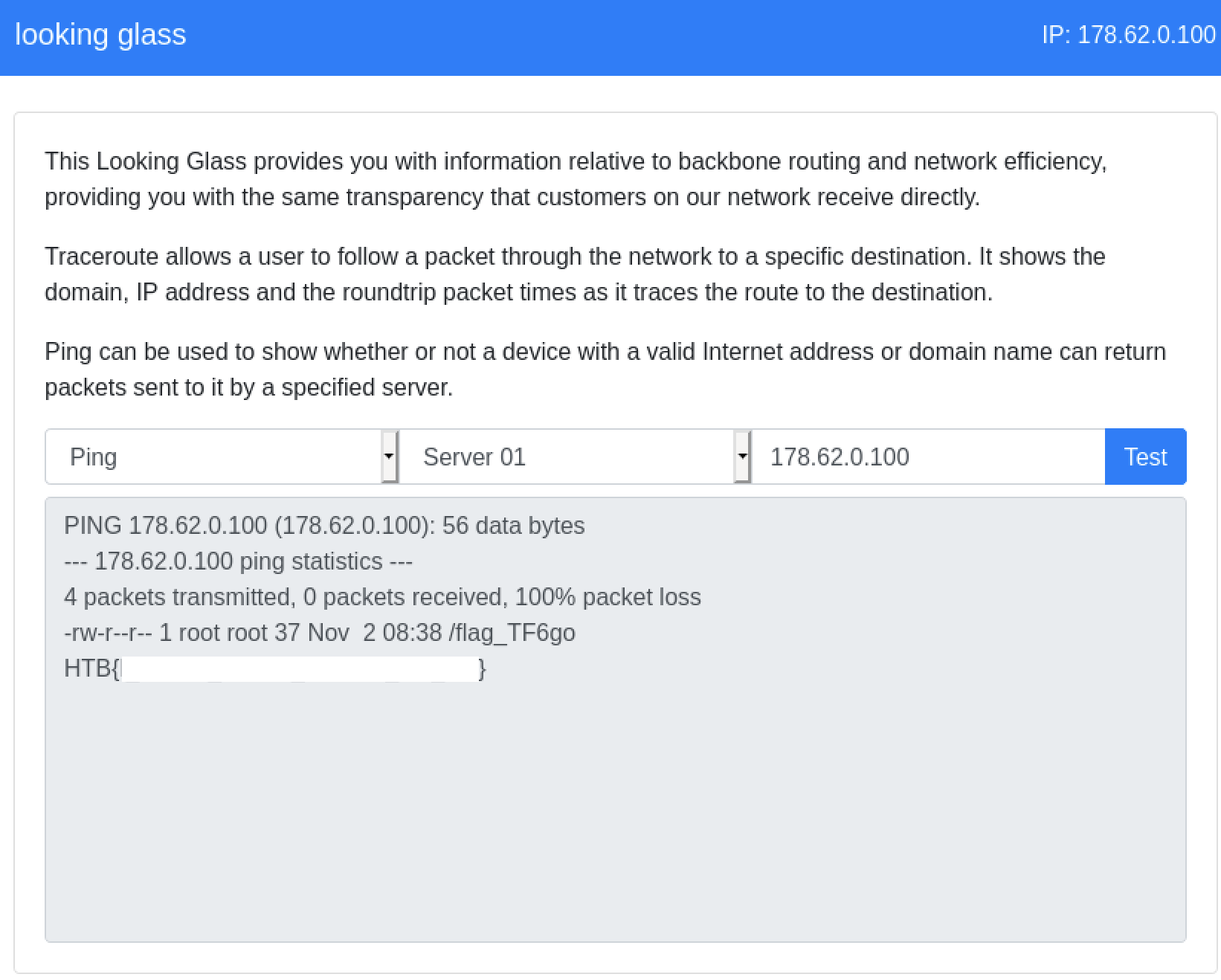
HackTheBox: Looking Glass Web Challenge
Today we will be walking through the ‘Looking Glass’ web challenge from HackTheBox. This specific challenge is[…]
2020 Quarantine CTF
In honor of social distancing, I will be hosting a remote quarantine CTF Thursday, April 2nd, 2020[…]

Zero-Day Research: Mechanical Keyboard Finder Version 4.31
Introduction In this edition of Zero-Day Research, I happen to come across a DOM-based Cross Site Scripting Vulnerability[…]
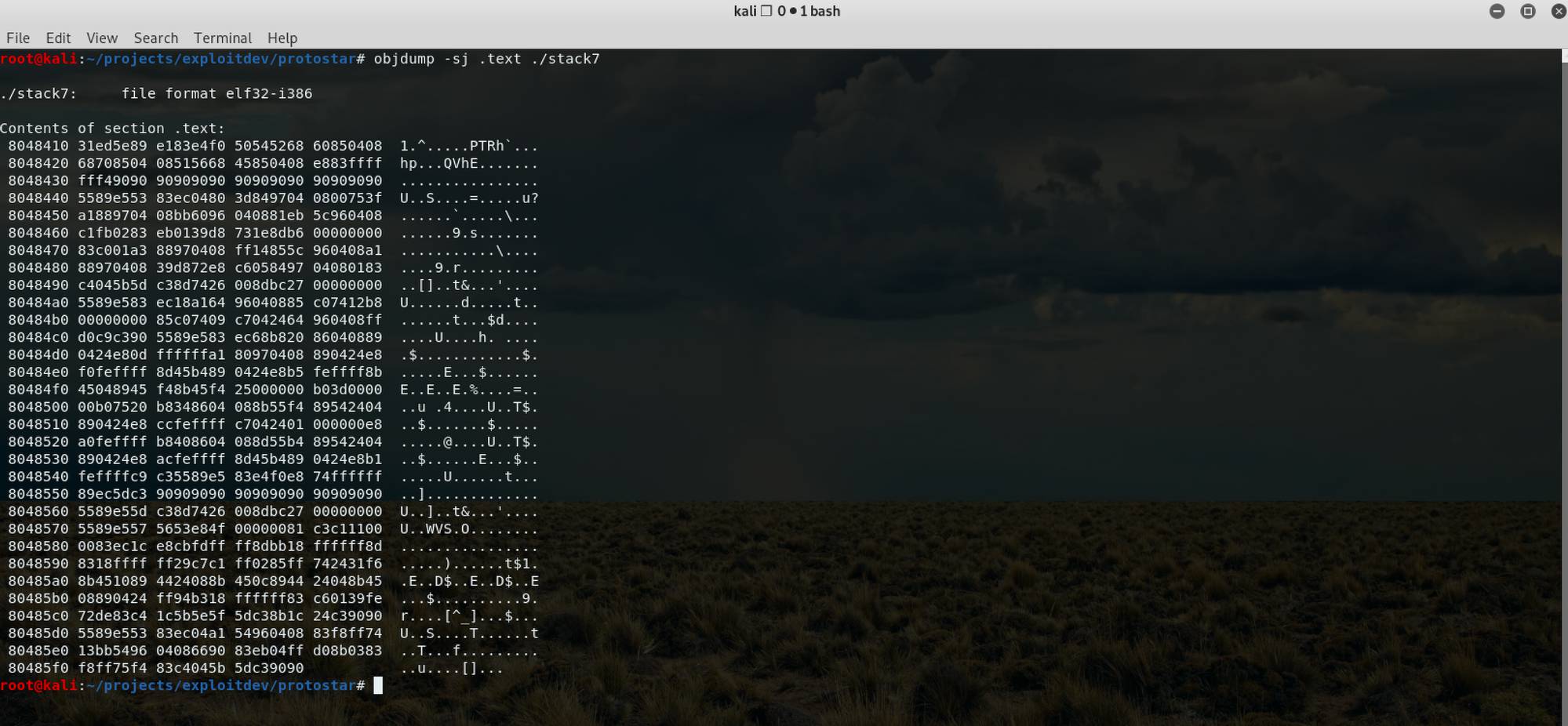
Return to .Text
Prerequisites In this article, we are going to quickly discuss a ROP technique called ‘return to .text’[…]

Defcon 27: Hacking the Badge
What did we do? We made modifications to the DEFCON27 Badge and turned it into a ‘Jackp0t’[…]

Zero-Day Research: ICSA-19-113-01 Rockwell Automation MicroLogix 1400 and CompactLogix 5370 Controllers
Background As technology continues to advance and more devices become networked together, new vulnerabilities will inevitably rise[…]