PicoC is a miniature code interpreter developed for C scripting. According to their documentation, PicoC was first written as the scripting language for a UAV’s on-board flight system. In this zero-day post we are going to speedrun the discovery of a null pointer dereference (CWE-476) denial of service (DoS) vulnerability in the PicoC interpreter. I discovered the vulnerability using AFL++ and notified the development team immediately. The DoS vulnerability affects PicoC up to version 3.2.2.
Prerequisites
- C Programming and Compilation
- Pointer Dereferencing
- Basic Understanding of AFL++
- Denial of Service Vulnerabilities
Disclosure and Disclaimer
The null pointer dereference vulnerability was responsibly disclosed to the PicoC development team. This post was intended for developers who are interested in keeping their applications secure and is for EDUCATIONAL PURPOSES ONLY. I do not condone illegal activity and cannot be held responsible for the misuse of this information.
Speedrun
Let’s get started…
Browse to the PicoC Source Code Directory
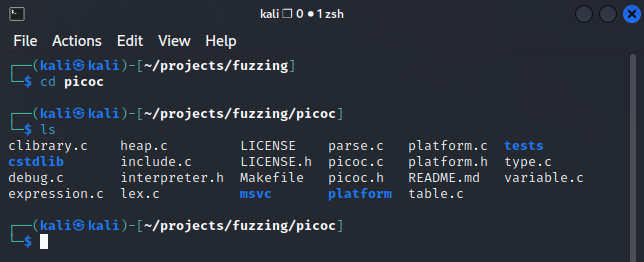
Point the Compiler Variable in the Makefile Towards ‘afl-clang-fast‘
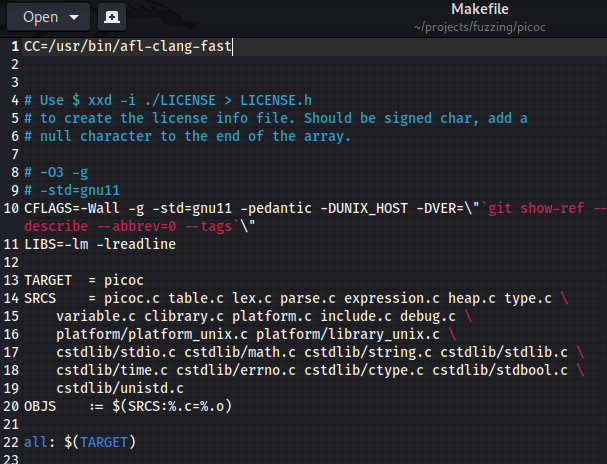
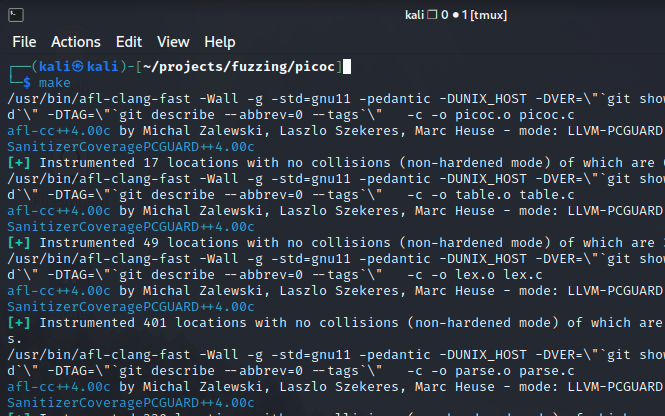
Run the ‘Make’ Command to Build Our Executable
Creating Input/Output Directories and Input Files
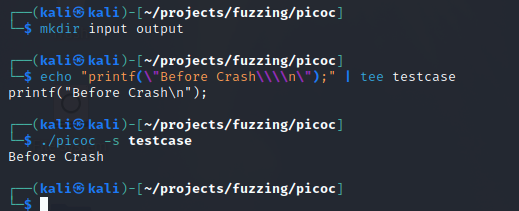
Moving Our Input File to the Input Directory and Starting AFL-Fuzz
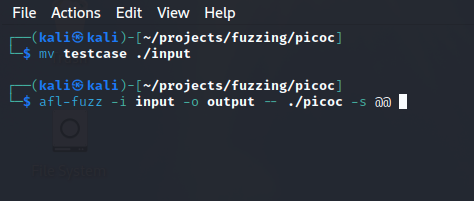
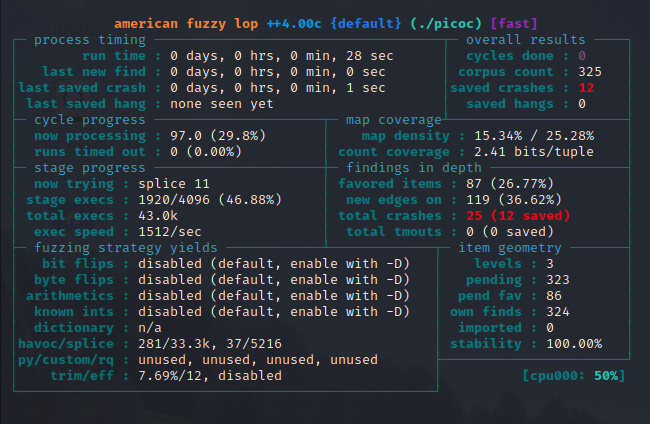
Scanning the Output For Crashes
Listing the ‘output/default/crashes’ Directory
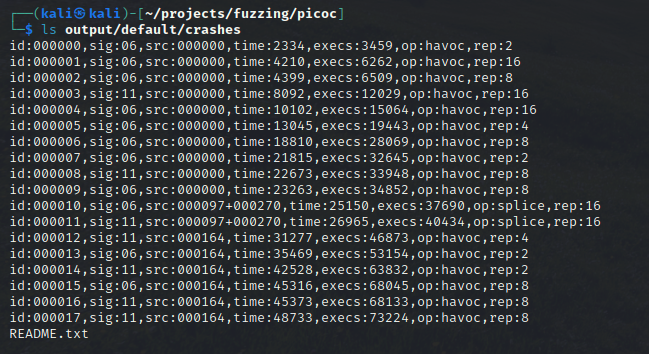
After opening the crash files we find an interesting crash input:
**4%;Replicating the Crash With GDB and Verifying the Null Pointer Dereference
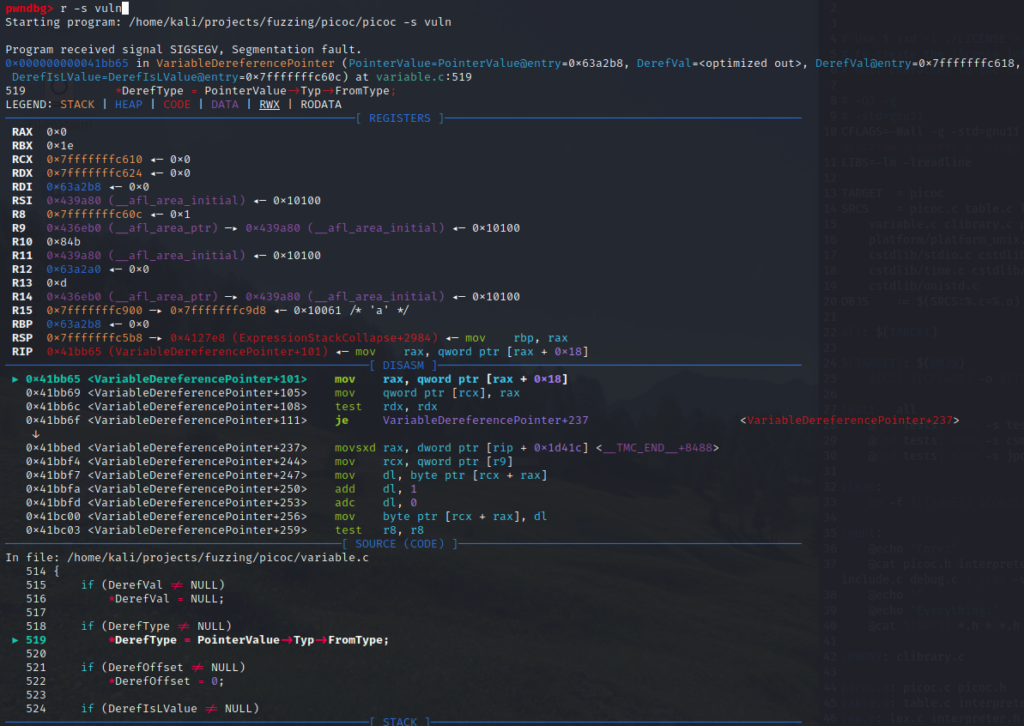
Speedrun Complete


No responses yet